- Home
- Blog
- Web Design 12 Essential Security Tips and Tricks for WordPress
12 Essential Security Tips and Tricks for WordPress
-
 11 min. read
11 min. read
-
 William Craig
William Craig CEO & Co-Founder
CEO & Co-Founder
- President of WebFX. Bill has over 25 years of experience in the Internet marketing industry specializing in SEO, UX, information architecture, marketing automation and more. William’s background in scientific computing and education from Shippensburg and MIT provided the foundation for MarketingCloudFX and other key research and development projects at WebFX.
WordPress is a great publishing platform, but it isn’t immune to all the potential attacks from hackers, spammers, and other ill-intentioned attackers trying to compromise the security of your WordPress installation.  WordPress being open source means that the chances of malicious attacks being successful are higher because the project’s source code can be easily obtained and studied for vulnerabilities. However, the good news is that there are steps that you can take to give your WordPress sites an extra layer of security.
WordPress being open source means that the chances of malicious attacks being successful are higher because the project’s source code can be easily obtained and studied for vulnerabilities. However, the good news is that there are steps that you can take to give your WordPress sites an extra layer of security.
This article highlights several tips and tricks that you can use to secure and lock down your WordPress site and to fortify it from attacks.
1. Back up your MySQL database regularly
You should always back up your site files and database. You should get into the practice of regular MySQL database backups by exporting your MySQL data as a .sql file to be stored in a safe location. 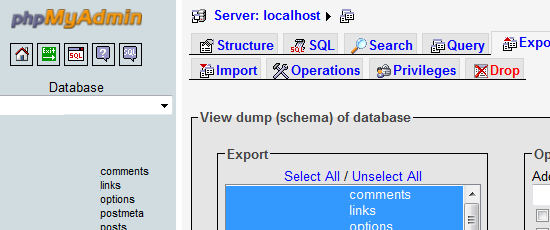 I recommend at least making daily backups of your database; even if you are not updating your site often, you will be getting user comments and trackbacks all the time.
I recommend at least making daily backups of your database; even if you are not updating your site often, you will be getting user comments and trackbacks all the time.
But manual backups are tedious and you’ll likely forget it or not do it regularly enough. To combat the human tendency to forget or put off boring and repetitive tasks, you should automate this process. You can use the plugin called WordPress Database Backup to automate your backups.
You can choose to make backups as often as you like and it provides you options such as hourly, daily, weekly, and monthly intervals. This puts you on the safe side because if your site’s database is compromised, you’ll have a backup to restore it to. There are other tools you can use for database backup automation, so explore your options and choose a method that works for you.
2. Take extra measures to secure your wp-admin folder
 The wp-admin folder is a very important folder because it contains all of the files that deal with administration. If the security of the files in it is compromised, bad things can happen not only to your WordPress installation but to the other information that’s on your domain. You have several options available to you for making sure this folder is locked down tight.
The wp-admin folder is a very important folder because it contains all of the files that deal with administration. If the security of the files in it is compromised, bad things can happen not only to your WordPress installation but to the other information that’s on your domain. You have several options available to you for making sure this folder is locked down tight.
We’ll talk about a couple of them here. One effective option to reducing the risk of a security breach on the wp-admin folder is by limiting the IP addresses that can access it via an .htaccess file (for Apache web servers). If you run another type of web server besides Apache (like IIS, which typically comes with a nice GUI out of the box), you may have to look into how to do similar permissions directives on your wp-admin folder.
To start, create a new blank document in your favorite text or source code editor (yes, this will work even if you use a simple text editor like Windows Notepad). Save this file with the name: .htaccess. You can place directives similar to the code block below in your .htaccess file (modified from an excellent article on the BlogSecurity site, called “Hardening WordPress with htaccess”).
order deny, allow allow from 123.456.78 #Your IP Address deny from all
Save the file and place it inside your wp-admin folder.
This option is nice and really tightens the security of your wp-admin folder, but it’s inconvenient if you work from multiple locations with different IP addresses.
Another way to add an extra layer of security to WordPress admin files is a WordPress security plugin called AskApachePasswordProtect. The plugin gives you several additional security features such as requiring a username and password to access any administrative pages. It also writes the .htaccess file for you automatically (which is great if you’re not familiar with working on access control on Apache servers).
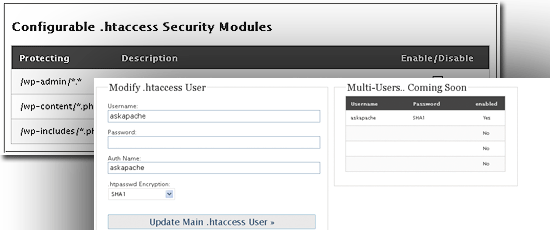 Check the documentation on the Apache site regarding how to use Authentication, Authorization, and Access control to see how you can lock down other folders of your WP installation, as well as other locations outside of your WordPress install.
Check the documentation on the Apache site regarding how to use Authentication, Authorization, and Access control to see how you can lock down other folders of your WP installation, as well as other locations outside of your WordPress install.
WordPress plugins are particularly useful in helping you protect your site. In fact, the Wordfence Security plugin has blocked more than 18.5 billion password attack requests. With WordPress statistics like that, using a plugin to help protect your site from attacks is a no brainer.
3. Don’t display your WordPress version number publicly
Many WordPress developers often display the WordPress version in the source code. But having this information publicly available makes it easy for attackers to exploit known vulnerabilities on a particular WordPress version. It is safer altogether to remove this code.
To do so, in your theme’s header.php file, look for code that looks something like the following code block and then remove it:
<meta name="generator" content="WordPress <?php bloginfo('version'); ?>" /> <!-– leave this for stats please -->If you can’t find the above code, yet you’re still seeing the meta generator tag in your site’s source, try looking for a PHP function call in your <head> tags.
<?php wp_head(); ?>
Study what things this function outputs for you, and just hardcode them into your theme files since these values will unlikely change. By default, this function outputs something like the following code block in your HTML source code:
<link rel="EditURI" type="application/rsd+xml" title="RSD" href="http://example.com/xmlrpc.php?rsd" /> <link rel="wlwmanifest" type="application/wlwmanifest+xml" href="http://example.com/wp-includes/wlwmanifest.xml" /> <meta name="generator" content="WordPress #versionnumber" />
Just hardcode the first two lines (if you even need them). This has the added benefit of reducing server overhead due to this limited-purpose function call.
4. Keep your WordPress installation up to date
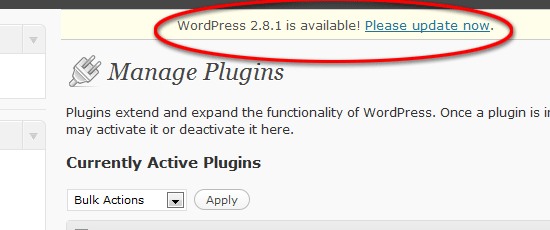 Since WordPress is an open-source project, it is easier to find vulnerabilities in its source code. To make sure that you’re using the most secure version of WordPress, update your installation as soon as you can whenever the stable release launches. You are taking unnecessary risks by not updating so if you have a WordPress installation that is at least two versions old, update it today!
Since WordPress is an open-source project, it is easier to find vulnerabilities in its source code. To make sure that you’re using the most secure version of WordPress, update your installation as soon as you can whenever the stable release launches. You are taking unnecessary risks by not updating so if you have a WordPress installation that is at least two versions old, update it today!
It literally takes 5 minutes according to WordPress.
5. Don’t use (or better yet, remove) the default “admin” username
When you install WordPress, it automatically generates a user with Administrator-level permissions called admin. It is strongly recommended that you do not use this username to make it harder for the hacker to guess your username and password via Brute force attacks. Even if you downgrade its permission role, it’s still a better idea just to remove this user altogether.
To delete the admin user, first, create a new user with the Administrator role through your WordPress Admin Panel (name it something that can’t be easily guessed). Then, with the newly-created user, delete the admin user. This technique saves you from doing this via MySQL query (or a MySQL GUI like phpMyAdmin).
In the subject of brute force attacks, you should also consider installing the Login Lockdown Plugin, which records the IP address and timestamp of every failed WordPress login attempt. If more than a certain number of failed attempts are detected from a particular IP address in short intervals, that IP address is blocked and no further login attempts are permitted from that address. You can configure this threshold to your preferences.
6. Encrypt your WordPress-related cookies
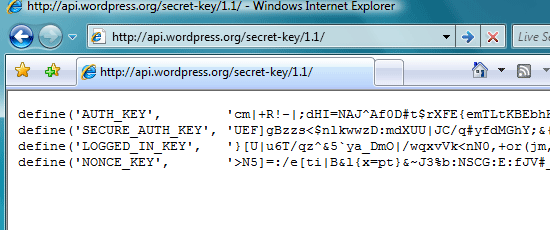 Another way to make your WordPress install secure is by encrypting the information stored in your WordPress cookies. This can easily be done using WordPress secret key generation tool. Get the random code from there, and paste it into your wp-config.php file.
Another way to make your WordPress install secure is by encrypting the information stored in your WordPress cookies. This can easily be done using WordPress secret key generation tool. Get the random code from there, and paste it into your wp-config.php file.
This makes it hard to gain access to your WordPress administration panel by way of cookie hijacking.
7. Use a strong password
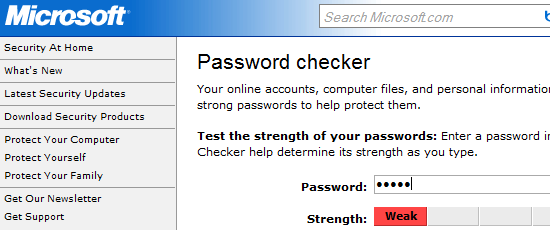 Utilizing a complex password is probably one of the easiest preventative steps you can take towards improving the security of your WordPress install. There many tools available on the web for verifying how strong your password is. For example, Microsoft has a free web-based tool on their site called Password checker.
Utilizing a complex password is probably one of the easiest preventative steps you can take towards improving the security of your WordPress install. There many tools available on the web for verifying how strong your password is. For example, Microsoft has a free web-based tool on their site called Password checker.
WordPress also has a built-in password strength verifier: please use it. Check out this nice guide on choosing a strong password at the Blog Herald.
8. Change your WordPress database table prefix from default settings
By default, WordPress uses wp_ as the table prefix for your MySQL database tables. To add a bit of security against SQL injection attempts, change this default value to something else. WordPress recommends that you keep the prefix you choose to only to numbers and letters.
I suggest changing it to something meaningful only to you like w0rdprss_ or yourblogname_. To change the prefix, head over to your wp-config.php file and change the table prefix value.
$table_prefix = 'wp_';
Note that if you already have a previous installation of WordPress, you have to change your database table name to the prefix you assigned in wp-config.php or your site will stop working.
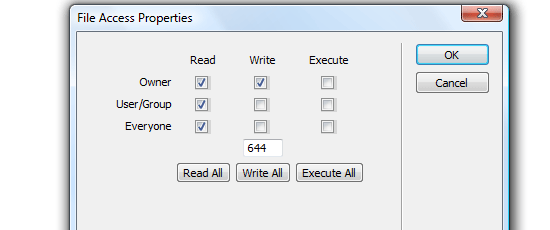
9. Use correct file permissions on your WordPress files
You need to make sure that all the files on your server have the right access rules in place. It is recommended that you don’t allow write access to any of your publicly accessible files, but some WordPress plugins require that certain files and folders are writeable. Configure your installation such that you only give all your files the minimum required permission.
Usually, a CHMOD value of 644 (which means that the file is read-only) is enough. You should be concerned if you have to set a file to a CHMOD value of 777 (which means anyone can read, write, and execute it). The way to determine if your site is at risk is to use a plugin called WP-Scan.
This plugin scans for weaknesses in your WordPress blog related to file permissions (among other things).
10. Limit what search engine spiders can index
Your entire site doesn’t need to be indexed by search engine spiders (search engines are known to make it easy for attackers to find vulnerable and sensitive files via advanced search syntax). One way to do this is by limiting search engine spiders to indexing only relevant files and folders on your domain. In the example below, you are telling search engines not to index anything inside folders that begin with the prefix /wp- (such as wp-login.php).
Disallow: /wp-*
You should read the tutorial on AskApache.com about WordPress robots.txt to learn about this subject in greater detail.
11. Use secured connections for accessing WordPress Admin pages
You can log in to the WordPress Admin Panel through encrypted SSL connections. You need to see if your web host service gives you access to an SSL certificate first. Most likely, you won’t, but they’re cheap enough to have and worth spending a few bucks on.
Once you have an SSL connection, you can run your sessions on https:// instead of http:// protocols by forcing SSL connections on admin-related pages and functions. You can do this by going into your wp-config file and inserting the following code:
define('FORCE_SSL_ADMIN', true);12. Lockdown world-access to your wp-config.php file
As you can see from the tips discussed above, the wp-config.php file is an integral part of your WordPress install. It contains sensitive data such as your database username and password (which is used by WordPress to create a database connection to WordPress tables). One thing you can do is to block world-access to the wp-config file is via .htaccess directives (for Apache servers).
You can use the following code block as an example.
<files wp-config.php> Order deny,allow deny from all </files>
Another thing you can do is to move your wp-config.php file to a directory above the default install location. This might seem strange, but according to the Official WordPress Codex article on hardening your security, it’s something you can do to reduce security compromises. Moving your config file adds an extra layer of security through obfuscation that can discourage many attackers.
Got more tips to share?
If you have more tips and WordPress hacks to secure it – please share it with all of us in the comments.
Related content
- 10 WordPress Plugins Guaranteed to Save You Time
- Using XAMPP for Local WordPress Theme Development
- 40 Excellent Free WordPress Themes
-
 President of WebFX. Bill has over 25 years of experience in the Internet marketing industry specializing in SEO, UX, information architecture, marketing automation and more. William’s background in scientific computing and education from Shippensburg and MIT provided the foundation for MarketingCloudFX and other key research and development projects at WebFX.
President of WebFX. Bill has over 25 years of experience in the Internet marketing industry specializing in SEO, UX, information architecture, marketing automation and more. William’s background in scientific computing and education from Shippensburg and MIT provided the foundation for MarketingCloudFX and other key research and development projects at WebFX. -

WebFX is a full-service marketing agency with 1,100+ client reviews and a 4.9-star rating on Clutch! Find out how our expert team and revenue-accelerating tech can drive results for you! Learn more
Make estimating web design costs easy
Website design costs can be tricky to nail down. Get an instant estimate for a custom web design with our free website design cost calculator!
Try Our Free Web Design Cost Calculator


Web Design Calculator
Use our free tool to get a free, instant quote in under 60 seconds.
View Web Design CalculatorMake estimating web design costs easy
Website design costs can be tricky to nail down. Get an instant estimate for a custom web design with our free website design cost calculator!
Try Our Free Web Design Cost Calculator