-
 3 min. read
3 min. read
-
 Trevin Shirey
Trevin Shirey VP of Marketing
VP of Marketing
- Trevin serves as the VP of Marketing at WebFX. He has worked on over 450 marketing campaigns and has been building websites for over 25 years. His work has been featured by Search Engine Land, USA Today, Fast Company and Inc.
Is my site hacked? How can I protect my website and business online? These are all common questions business owners and managers ask.
It’s common sense these days for businesses and individuals to utilize several layers of security protection for their computers, networks, servers and hard drives.
The network security market has been growing for years and, even with the transition to cloud-based computing, the security software market grew from $7.5 billion in 2005 to an estimated $16.4 billion in 2010.
Despite implementing all of this security protection, no amount of money can stop the biggest danger to your digital security.
I’m not talking about a world-class hacker, or Firesheep or even some newfangled polymorphic virus. The biggest threat to your digital security is yourself. (I found this out the hard way when my email was hacked.)
I recently picked up “The Art of Deception” by Kevin Mitnick, perhaps the most prolific hacker of all time.
Mitnick details the importance of the human element of security and tells story after story of how computer-related hacks were pulled off through social engineering, not technical expertise. Mitnick used social engineering to ride the LA bus system for free, make free cell phone calls and gain access to numerous corporate networks.
The common myth goes something like this: “the only safe computer is one that is turned off,” but Mitnick argues this is a false statement because a skilled hacker would find a way to persuade the owner to turn the computer on. Perhaps the scariest recurring theme from the book is how often hackers would simply ask for information and the victim would just hand it over, no questions asked.
Let’s look specifically at the corporate world for a moment.
No matter the industry, if you have customers or clients, you are in possession of some pretty delicate personal data. Client contact information. Checks.
Credit card numbers.
There are a lot of things that could be dangerous in the hands of the wrong person. While these examples may be more obvious, many times the ‘innocuous’ info actually presents the biggest threat; spouse’s name, department name, phone extensions, co-workers, account or store numbers.
One common “hack” is to get a manager’s name and a store number of a franchise and then impersonate them. In “The Art of Deception,” a hacker bets his father $50 that he can get his credit card information by making only one phone call.
He calls a local video rental store his father uses and identifies himself as a manager at a nearby branch of the same store.
He tells them his father is waiting in line at his branch of the store and he needed to verify his card on file at the other branch. The video store then reads off his credit card number and the stunned father handed over $50.
Another example: After learning the names and contact information for a few recent employees of a large company, the hacker would call them and identify himself as somebody from the company’s IT department calling to walk them through some of the best practices for security. Eventually, the hacker would con them into changing their password to one suggested by the ‘IT department’.
Ouch. These social engineering hacks can seem impossible to prevent. After all, some information like store number or job title is pretty much out in the open.
But by no means does that suggest it’s alright to be oblivious to the threats out there.
Companies ought to have detailed policies on security and information disclosure and enforce them.
Employees should report suspicious calls and shift technical questions to qualified personnel. In addition, always be wary of revealing sensitive or technical information over the phone. Depending on the industry you work in, the chances of this kind of social engineering attack happening to you or your company may be slim.
However, it’s important to know and remember there’s another face to security beyond the technical side.
For as much money as we all pour into security, it would be foolish to neglect the human element of things.
-
 Trevin serves as the VP of Marketing at WebFX. He has worked on over 450 marketing campaigns and has been building websites for over 25 years. His work has been featured by Search Engine Land, USA Today, Fast Company and Inc.
Trevin serves as the VP of Marketing at WebFX. He has worked on over 450 marketing campaigns and has been building websites for over 25 years. His work has been featured by Search Engine Land, USA Today, Fast Company and Inc. -

WebFX is a full-service marketing agency with 1,100+ client reviews and a 4.9-star rating on Clutch! Find out how our expert team and revenue-accelerating tech can drive results for you! Learn more
The Internet in Real Time
Ever wonder how much is going on at once on the Internet? It can be tough to wrap your mind around it, but we’ve put together a nice visual that’ll help! The numbers show no sign of slowing down either.
Find out More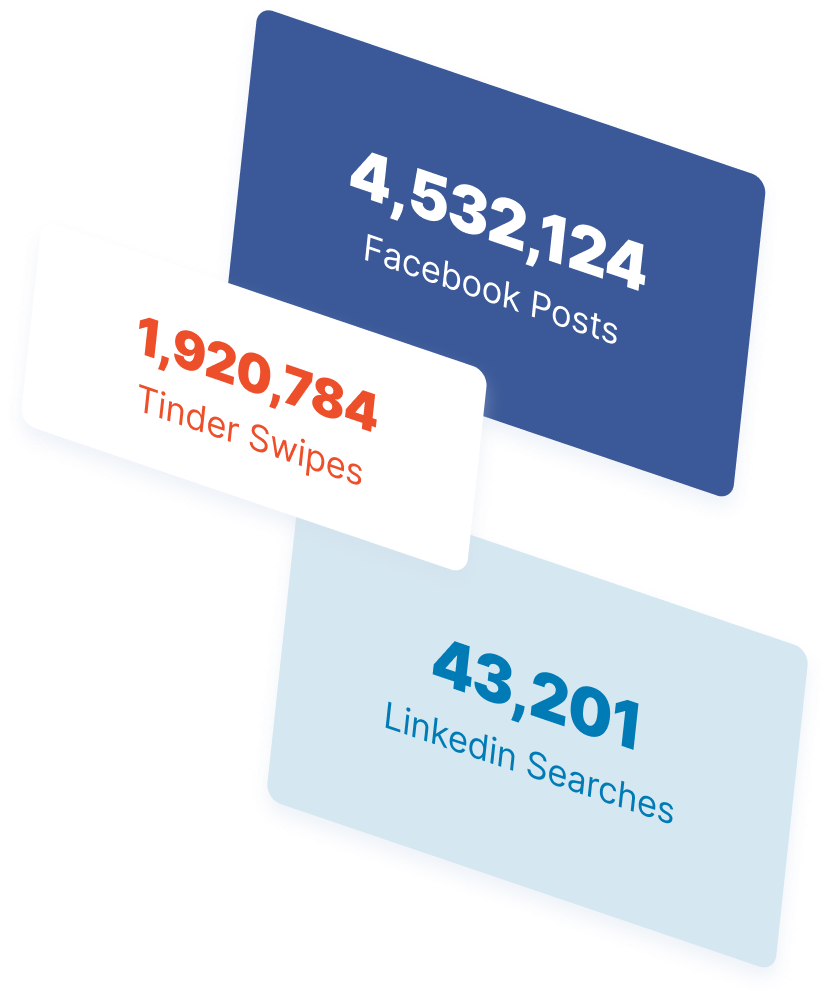

Ready to Drive Results for Your Business?
See how WebFX uses SEO, PPC, Social Media, and Web Design to Drive Revenue for Businesses.
Get InspiredThe Internet in Real Time
Ever wonder how much is going on at once on the Internet? It can be tough to wrap your mind around it, but we’ve put together a nice visual that’ll help! The numbers show no sign of slowing down either.
Find out More